(Dublin, Ireland) ▲
The 7th International Conference on Artificial Intelligence and Security (ICAIS 2021), will be held in Dublin, Ireland, in July 2021. Over the past six years, ICAIS has become a leading conference on artificial intelligence and security, garnering comprehensive coverage in July 2019 by Reuters and in June 2018 by CCTV 4 China News. ICAIS is a highly selective and premier international forum on computer science and engineering research. In addition to the main sessions, the conference will include workshops, panels, demonstrations, and exhibits. The organizing committee is excited to invite you to take part in ICAIS 2021, to discuss issues at the technological frontier of society today as well as interdisciplinary technological trends.

(ICAIS 2020)
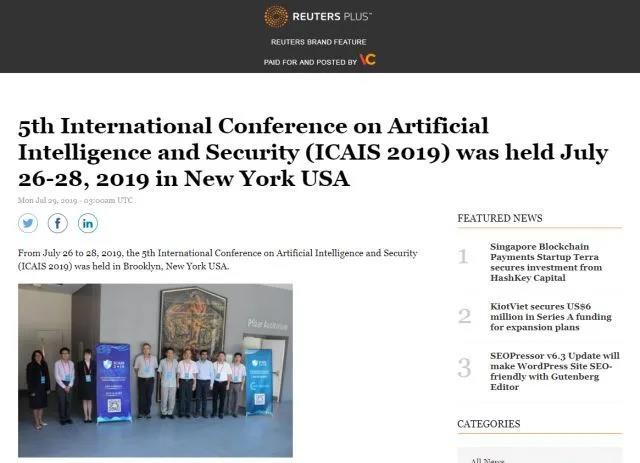
(Reuters reported the ICAIS 2019)
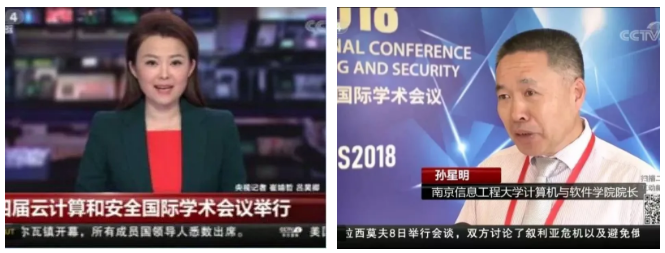
(CCTV 4 China News reported the ICCCS 2018)
We invite proposals for workshops that will provide forums for researchers, engineers and scientists from all communities (academia, industry, standards organizations) to present their latest research findings, novel ideas, and valuable comments in specific areas of interests.
Topics
Topics of interest include, but are not limited to:
1.Artificial Intelligence
Machine Learning
Natural Language Processing
Computer Vision
Data Mining
Artificial Neural Networks
Affective Computing
Multiagent Systems
Planning
Knowledge Representation
Reasoning
Robotics and Reception
Artificial Intelligence Applications in Science, Engineering, Healthcare and Medicine
2. Big Data
Techniques, Models and Algorithms for Big Data
Tools and Systems for Big Data
Big Data Analytics and Social Media
Hardware/Software Infrastructure for Big Data
Mobile Communications and Networks
Security and Privacy for Big Data
Copyright Protection for Big Data
Data Compression
Machine Learning and AI for Big Data
Big Data Persistence and Preservation
Big Data Quality and Provenance Control
Big Data Storage and Retrieval
Big Data Applications
3. Cloud Computing and Security
Cloud Computing Architecture and Systems
Cloud Computing Models, Simulations, Designs, and Paradigms
Cloud Management and Operations
Dynamic Resource Provision and Consuming
Cloud Computing Technologies, Services and Applications
Security Evaluation and Benchmarks Based on Cloud
Authentication, Authorization and Reliability Issues in Cloud
Security and Privacy in Cloud Computing
4. Information Hiding
Coverless Information Hiding
Steganography and Steganalysis
Digital Watermarking, Fingerprinting and Forensics
Multimedia Authentication and Encryption
Covert/Subliminal Channels
5. IoT Security
Data Security and Privacy in the IoT
Attacks and Countermeasures on IoT Systems
Trust Model, Data Aggregation and Information Sharing
Secure Hardware and Software for IoT
Application Security for IoT
6. Multimedia Forensics
Active and Passive Forensics
Big Data Forensics
Portable electronic device forensics
Network Forensics
Anti-forensics
7. Encryption and Cybersecurity
Measurements for Cybersecurity
Post Quantum Cybersecurity
Visualization for Security
Applied Cryptography
Language-based Security
8. Block Chain Technology
Block chain Technology Innovation and Application
Block chain Encryption
Block chain Privacy Protection
Block chain Auditing and Forensics
Block chain and Bitcoin Security
Benefits of Accepted Workshop Proposal
Provide same benefits with the main conference;
Accepted outstanding papers could be recommended to be published in SCI indexed journals;
Accepted regular papers could be published on LNCS (EI indexed);
Accepted short papers could be published on international academic journals.
Submission Guidelines
Title;
Abstract: 200 word summary of the workshop purpose;
Topics: What topics of interest will be covered by the workshop;
Chair(s): Name, affiliation, email address, homepage and short (one paragraph) biography of each chair (at least one member of chairs comes from oversea);
Program Committee: Names and affiliations of potential PC members.
Proposal Submission:Please download ICAIS workshop template in our official website and send to Prof.Baowei Wang, Email: wang@nuist.edu.cn or Prof.Lingyun Xiang,Email: xiangly210@163.com
Review Criteria
The decision on acceptance or rejection of a workshop proposal will be made on the basis of the overall quality of the proposal and its appeal to a reasonable fraction of the artificial intelligence, cloud computing, and cyber security community. Other factors, such as overlap with other workshop proposals, or the number of attendances, will also be taken into account when making the final decision.

(ICAIS 2020)
The workshop organizer(s) will be responsible for promoting the workshops in communities and moderating the workshop.
Publication
Important Dates
Workshop proposals due: | August 10, 2020 |
Notification of accepted proposals: | August 15, 2020 |
Contact Information
Prof.Baowei Wang, ICAIS 2021 Workshop Chair.
Email: wang@nuist.edu.cn
Prof.Lingyun Xiang, ICAIS 2021 Workshop Chair.
Email: xiangly210@163.com